Open Source Web Traffic Management
A flexible stream processor for developers to analyze and control web traffic.
Download beta from GitHub Get cloud hosted instance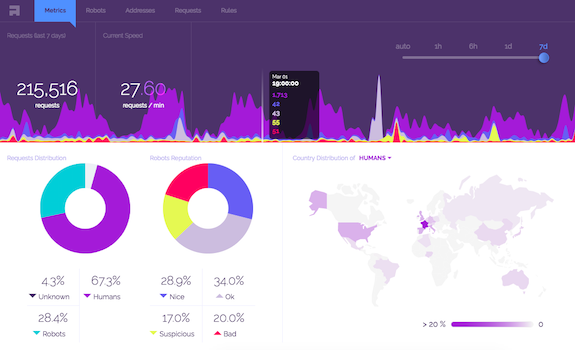
Precise Metrics
Unique dashboard bringing key metrics not seen in other monitoring tools.
- Requests per second.
- Human vs robot split.
- Robot reputation breakdown.
- Zoom on specific timerange.
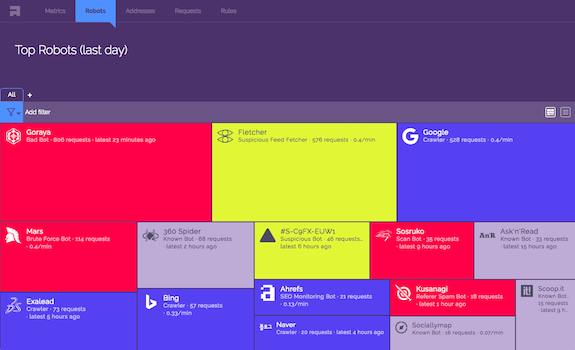
Robots Overview
Visualize the activity of robots on your server.
- Not just the well known crawlers, suspicious and bad robots too.
- Zoom on specific robot to get details and see its requests.
- Filter by timerange.
- Search and filter by any property. Save searches.
- Block the suspicious and bad one.
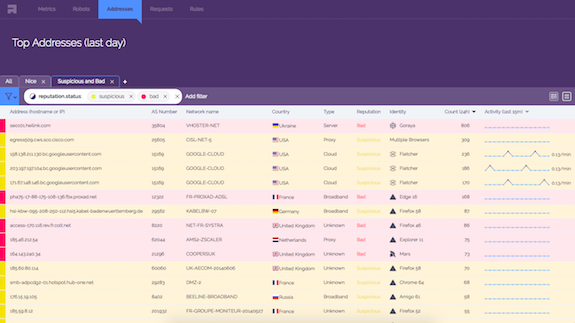
Active IP Addresses
Check the respective activity of IP addresses in real time.
- IP addresses are augmented with metadata:
- reverse hostname
- as number
- network name
- type
- reputation
- View and order by 24h count or 15m activity.
- Search and filter by any property. Save searches.
- Block the suspicious and bad one.
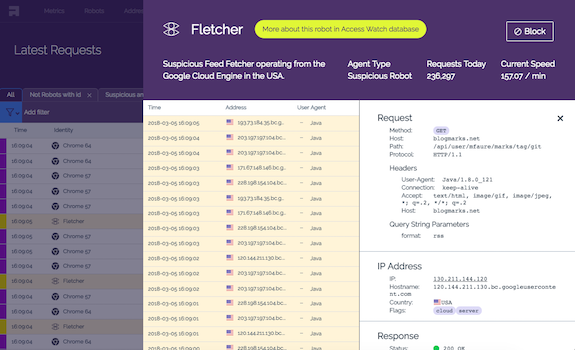
Request Details
Review all the incoming requests in real time
- Zoom on specific request to get its details
- Filter by timerange.
- Search and filter by any other property. Save searches.
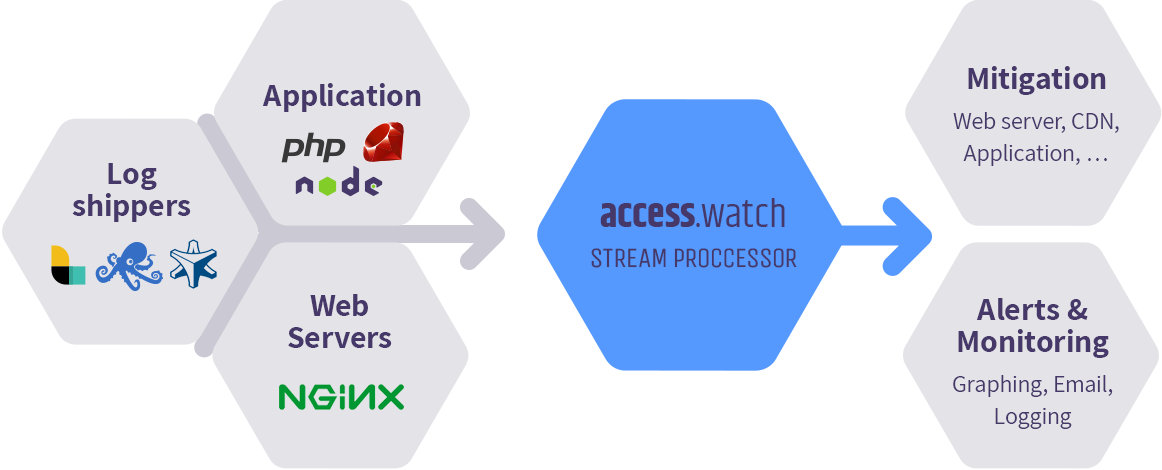
Flexible and Powerful
Connect your log data from any web server, log storage solution or database.
All visitor requests flow through the Access Watch stream processor to monitor traffic events and detect anomalies in real-time.
Automatically inject traffic rules and key data results into your existing infrastructure to control traffic.
Real-time Analysis
Feed your web traffic logs into Access Watch and get a real-time overview of visitors, bots and events in your traffic.
Traffic Control
Access Watch powers developers to easily manage rule sets to control web traffic and automatically output them into existing infrastructure.
Data Augmentation
Designed to easily connect to 3rd party feeds via APIs, libraries or plugins to enhance IP data, bot detection, security threats and more.